Unlocking the Power of Trezor Hardware Wallet: Your Ultimate Guide to Secure Cryptocurrency Storage
Introduction
As the world of cryptocurrencies continues to expand, the need for secure storage solutions becomes increasingly important. One such solution is the Trezor hardware wallet, a device designed to protect your digital assets from hackers and other malicious actors. In this article, we'll explore the features, benefits, and best practices of using a Trezor hardware wallet to keep your cryptocurrencies safe and sound.
What is a Trezor Hardware Wallet?
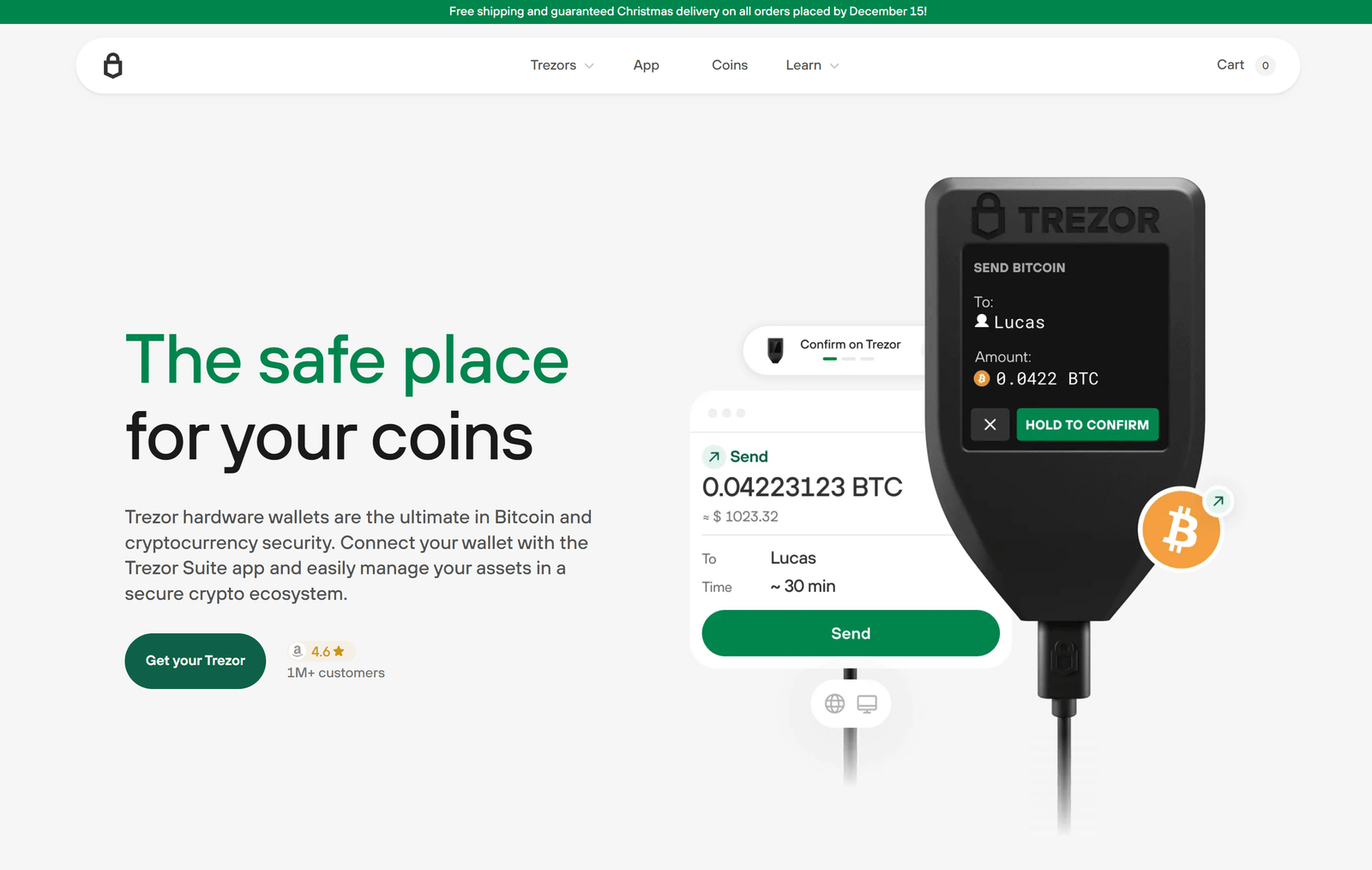
A Trezor hardware wallet is a physical device that stores your private keys offline, protecting them from online threats. It allows you to securely manage your cryptocurrencies without exposing your private keys to potential risks. Trezor wallets are compatible with various cryptocurrencies, including Bitcoin, Ethereum, Litecoin, and many others.
How does it work?
The Trezor hardware wallet works by generating and storing your private keys offline. When you want to make a transaction, you connect the device to your computer or mobile device and enter your PIN code. The Trezor then signs the transaction with your private key, ensuring that your funds are securely transferred without exposing your private key to the internet.
Benefits of using a Trezor Hardware Wallet
- Security: The primary benefit of using a Trezor hardware wallet is the enhanced security it provides. By keeping your private keys offline, you significantly reduce the risk of your funds being stolen by hackers or other malicious actors.
- Ease of use: Trezor wallets are designed to be user-friendly, making it easy for even novice users to manage their cryptocurrencies securely. The device comes with a simple, intuitive interface and clear instructions, ensuring a smooth user experience.
- Multi-currency support: Trezor wallets support a wide range of cryptocurrencies, allowing you to store and manage multiple digital assets within a single device.
- Open-source software: The Trezor hardware wallet is built on open-source software, which means that its code is freely available for review and improvement by the global community of developers. This ensures transparency and security, as any vulnerabilities can be quickly identified and addressed.
- Backup and recovery: In case your Trezor hardware wallet is lost, stolen, or damaged, you can easily recover your funds using the backup seed phrase. This phrase consists of a series of words that can be used to restore your private keys and access your cryptocurrencies on a new device.
Best Practices for Using a Trezor Hardware Wallet
- Keep your software up-to-date: Regularly update your Trezor wallet's firmware and software to ensure that you have the latest security patches and features.
- Use a strong PIN code: Choose a PIN code that is at least 6 digits long and contains a mix of letters, numbers, and symbols. Avoid using easily guessable PINs, such as birthdates or consecutive number sequences.
- Store your backup seed phrase securely: Your backup seed phrase is a crucial component of your Trezor wallet's security. Store it in a safe place, such as a locked drawer or a secure digital vault. Never share your seed phrase with anyone or store it on a computer or mobile device.
- Use a dedicated computer for cryptocurrency transactions: To minimize the risk of malware or other threats, consider using a dedicated computer or virtual machine for all your cryptocurrency transactions. This will help ensure that your Trezor wallet remains isolated from potential security risks.
- Double-check your transactions: Before confirming a transaction, always double-check the details, such as the recipient's address and the amount being sent. This will help prevent accidental mistakes or fraudulent activities.
Conclusion
A Trezor hardware wallet is an essential tool for anyone looking to securely store and manage their cryptocurrencies. With its robust security features, multi-currency support, and user-friendly interface, the Trezor wallet offers peace of mind for both novice and experienced cryptocurrency users alike. By following best practices and staying vigilant, you can ensure that your digital assets remain safe and secure in the ever-evolving world of cryptocurrencies.
Made in Typedream